VoIP is about convergence, saving telecom costs. However, these types of systems also create more inroads for attack & lose lot of money because of VOIP frauds & attacks. In this article, I will discuss a number of different ways your communications system can be breached and how it can be protected.
Is your IP Phone system a target for VOIP attacks?
Every year the number of PBX fraud victims increases dramatically. More and more companies are targeted by individuals who are looking to bring down or exploit the communications system. Some do it for fun and others for illicit profit, but the end result is always the same… It results in the telephone bill of average 5,000$ USD to 80,000$ per attack to your carrier!
The most vulnerable targets remain small-medium size businesses that are new to managing their own VOIP. They either don’t have the IT experience and staff to properly secure and maintain the network, or they’re unaware of the risks altogether having recently switched from a landline system. Whatever the reason, many networks are consistently left unprotected. By the time most companies realize that something is wrong with their phone expenses, it’s too late—the network security has been compromised.
Here is the article link which explain about the VOIP attacks: http://www.nytimes.com/2014/10/20/technology/dial-and-redial-phone-hackers-stealing-billions-.html?_r=0
Toll fraud losses are growing at rate faster than global telecom revenues.
Things to be considered
- The law is clear, you are the only responsible for the security of your phone system and any charges generated from it.
- You will pay on average 5,000$ USD to 80,000$ per attack to your carrier.
- Downtime of your whole system is very common.
- In some cases you will have to find a different carrier.
Let’s first discuss what steps you can take to protect your account from hackers.
What is STM and how it can help you secure your VOIP infrastructure?
You may be familiar with UTM – Unified Threat Management device, but have you come across an STM – SIP Threat Management device, that is used to protect the IP PBX and IP Phones/Telephony infrastructure from threats/attacks?
The STM – SIP Threat Management device, is installed in front of any SIP based PBX system or gateway and offers extra layers of Toll fraud losses are growing at rate faster than global telecom revenues.
Things to be considered
- The law is clear, you are the only responsible for the security of your phone system and any charges generated from it.
- You will pay on average 5,000$ USD to 80,000$ per attack to your carrier.
- Downtime of your whole system is very common.
- In some cases you will have to find a different carrier.
Let’s first discuss what steps you can take to protect your account from hackers.
What is STM and how it can help you secure your VOIP infrastructure?
You may be familiar with UTM – Unified Threat Management device, but have you come across an STM – SIP Threat Management device, that is used to protect the IP PBX and IP Phones/Telephony infrastructure from threats/attacks?
The STM – SIP Threat Management device, is installed in front of any SIP based PBX system or gateway and offers extra layers of security against numerous types of attacks that are targeted towards IP telephony infrastructure. The features offered by the STM complement those of a traditional firewall or UTM, and it can be installed in conjunction with a UTM.
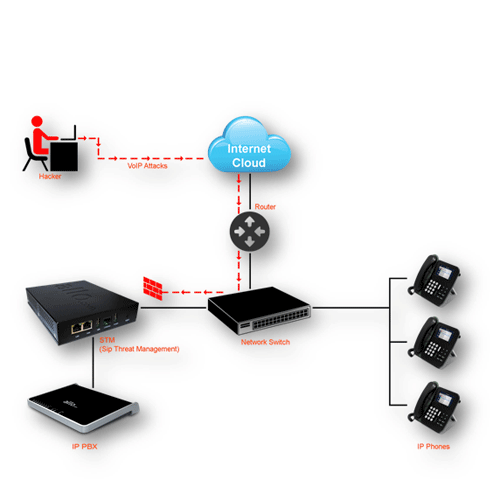
Typical STM Installation Diagram
Here is a diagram of a typical STM installation in a VOIP network:
- SIP Device Fingerprinting: The hacker will try to identify which PBX software is running or which hardware you are using. Once he gets this info, he will look for their weaknesses and attack accordingly. The STM will simply not answer to such requests leaving the hacker in the dark.
- User enumeration: The hacker will request the system to divulge the extension numbers. Once he gets this info, he can then start looking for the passwords. The STM will not give out this info.
- Password Cracking Attempt: The hacker will try different user names and passwords in order to gain access to an extension or the admin panel of the PBX. The STM can be configured to block an IP if more than 10 trials are done within 10 minutes, for example.
- PHREAKERs: These guys take advantage of your negligence and steal from you without really hacking anything… They just check the most common/default user names and passwords used and if they get lucky, it’s a bad day for the victim.
- The Hardcore Scammer: Using scripts and special tools, these criminals know exactly what they are doing and have the knowledge to hack and exploit an unprotected phone system. The list of scams they can run is long but it can range from setting up an extension in your system and using it to sell cheap international calls, to more elaborate FAX back or CALL back scams where they use your system to call very expensive / minute phone numbers they control…
- DoS/DDoS attacks: These are designed to flood your PBX with an exaggerated numbers of packets. Their goal is to bring down your communication system and render it unusable. The STM will dynamically block for a pre-determined period of time, the IP or IPs from which these attacks originate.
- Cross Site Scripting attacks: These are amongst the most complex and hard to achieve. A script is injected in your PBX by the hacker and can program it to do all kind of malicious actions such as having all your extensions ring at once. The STM blocks off the intent and IP address (es) trying to do that.
Manufacturer’s message: The ALLO.com STM uses the real-time deep packet inspection engine, which is in fact a large database of known threats to PBXs. Much like a terrorist watch list, the STM uses this list to check each SIP packet heading towards your system and blocks any malicious packet as well as its originating IP.
Instead of losing thousands of dollars due to the victim of VOIP attacks, invest on 300$ worth of ALLO STM, which is plug & play.
Investing in an STM to protect your communications network is a must.
Download
- Datasheet – Download Now
- User Manual – Download Now
- Quick Installation Guide – Download Now
User Interface
Access to GUI demo: Click Here
Username: admin
Password: admin